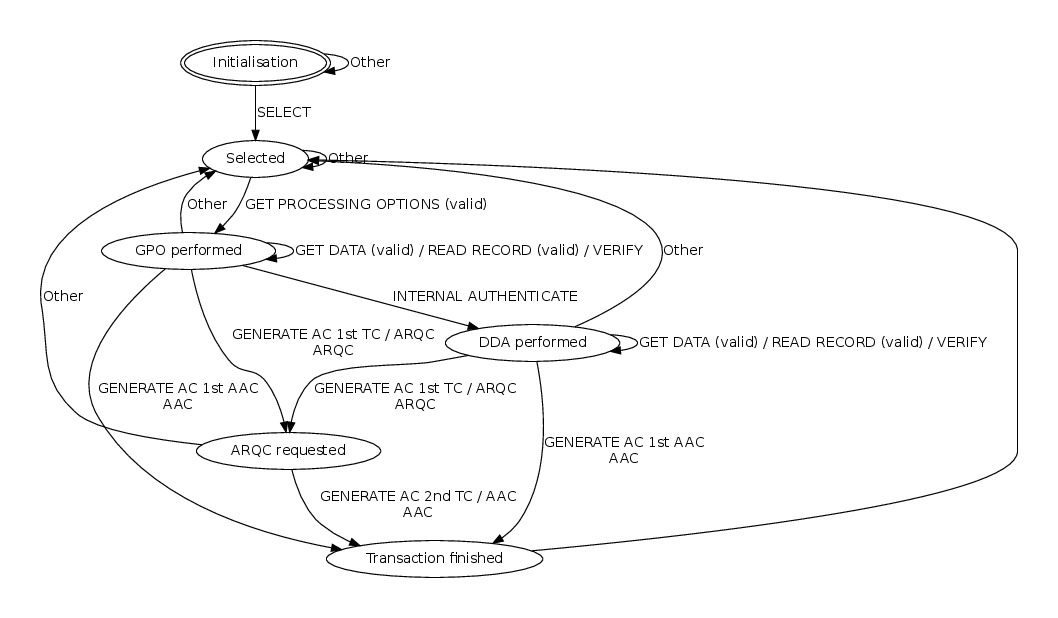
We have learned models for several client implementations, i.e. real bank cards from different banks. Access to the smart cards was realised via a standard smart card reader. The models might be incorrect, but already showed reproducible bugs in some cases.
| Benchmark Name | Model | Inputs/Outputs | States | Transitions | Publications |
|---|---|---|---|---|---|
| MAESTRO | dot-file | 14 / 10 | 6 | 84 | [ARP13] |
| MAESTRO (ASN) | dot-file | 14 / 10 | 6 | 84 | [ARP13] |
| MAESTRO (Rabo) | dot-file | 14 / 10 | 6 | 84 | [ARP13] |
| MAESTRO (Volksbank) | dot-file | 14 / 11 | 7 | 98 | [ARP13] |
| MasterCard | dot-file | 14 / 9 | 6 | 84 | [ARP13] |
| MasterCard | dot-file | 15 / 9 | 5 | 75 | [ARP13] |
| PIN | dot-file | 14 / 10 | 6 | 84 | [ARP13] |
| SecureCode | dot-file | 14 / 9 | 4 | 56 | [ARP13] |
| SecureCode (ASN) | dot-file | 14 / 9 | 4 | 56 | [ARP13] |
| SecureCode (Rabo) | dot-file | 15 / 12 | 6 | 90 | [ARP13] |
| VISA | dot-file | 15 / 11 | 9 | 135 | [ARP13] |
Some of the learned models listed in the table above are shown below :